
Enhancing Cloud Security Governance Strategies With Google Cloud Platform
Access Management and Regulatory Compliance in India
Securing access in the cloud is about far more than simply setting passwords. For Indian organizations using Google Cloud, Identity and Access Management (IAM) enables administrators to adhere to regulatory frameworks, including mandatory role segregation and frequent audit trails as imposed by Indian authorities.
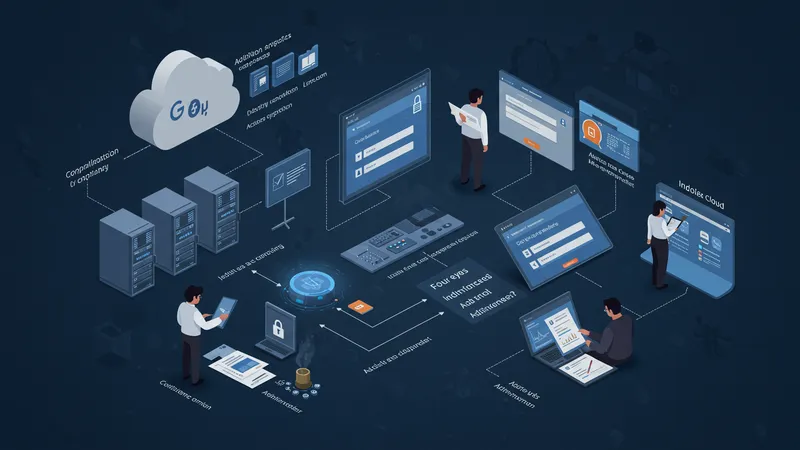
Google Cloud’s IAM supports fine-tuned control over resources, down to individual permissions, ensuring compliance with RBI and sector-specific guidelines. Indian banks, for example, can enforce “four-eyes” principles, requiring two administrators to approve sensitive changes, thus reducing the risk of insider threats.
Multi-factor authentication (MFA), recommended in the Indian Digital Personal Data Protection Bill, is easily implemented through GCP IAM, adding another layer of assurance for remote and mobile workforce scenarios common in India’s digital transformation landscape.
Logging and monitoring access events through Cloud Audit Logs simplifies forensic analysis and reporting. This is particularly beneficial for regulated industries in India, as organizations can demonstrate audit readiness and data-governance discipline as required by governing bodies.